Hidden cyber-hazard uncovered in time using ‘advanced Excel visualization’

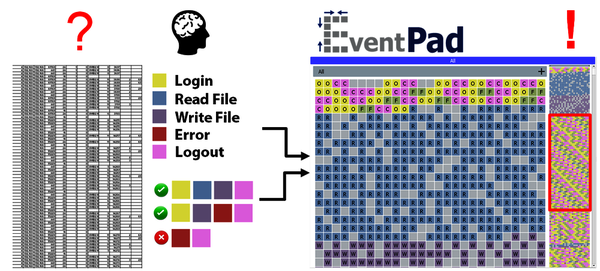
Nowadays, cyber-attacks are aimed at a single, powerful strike that causes major damage. They often take months of secret preparation. To uncover suspicious activity in data traffic in time, IT specialist Bram Cappers at Eindhoven University of Technology developed the visualization tool Eventpad. This tool converts a system’s complex data flows into a clear collection of colored blocks that easily reveals deviating or conspicuous patterns. Cappers successfully uncovered several forms of ransomware and telephone fraud with Eventpad. On 4 December, Cappers will graduate from TU/e with his tool, with which he has already begun a startup.
The destruction of a nuclear installation in Iran, the theft of 6.5 million log-ins from LinkedIn, a hacking attempt on the German parliament: these are large-scale cyber-attacks that feature almost daily in the news. Such attacks can occur because hackers have been secretly ‘rooting’ in computer networks and systems for months without anyone noticing.
Under the bonnet
“The problem with many companies is that systems have been developed over so many years that nobody understands exactly what is going on under the bonnet,” says Bram Cappers. According to him, this makes it difficult to determine whether or not data traffic belongs in the system, and thus when certain behavior can lead to dangerous situations.
Cappers developed Eventpad as a form of preventive security that makes the complex data flows in a computer system clear and understandable for the user. Based on the user's input, automated processes convert events in the system into long rows of brightly colored blocks. “This way, as a user, you can not only identify what is happening, but also why,” says Cappers. Suspicious or deviating patterns in the data become visible at a glance.
Telephone fraud and ransomware
During his PhD research – in which he built the tool from scratch – Cappers convincingly demonstrated that it works for various applications. For instance, he was able to demonstrate traces of fraud in the use of VoIP telephony. In this type of fraud, hackers try to gain access to telephone exchanges and earn money by calling their own premium numbers.
Using Eventpad, he illustrated the different steps during such a call, such as ringing the phone, the other side accepting the call and a closing signal. Each call was converted into a row of blocks, with the color of the blocks representing an action. Cappers: “It became clear that not all calls follow a logical pattern: something was wrong with that.”
He also visualized the operation of ransomware, malicious software that criminals use to lock files and then demand high ransom sums from victims to recover the files. “It was interesting that the way the viruses work leads to a specific and recognizable block pattern for each virus,” says Cappers. "This means that when mapping a computer network, you can immediately detect this ‘signature’ of the virus.”
Start-up and prizes
With Eventpad, Cappers previously won the IEEE Visual Analytics Challenge in 2017, and has this year won the ICT.OPEN Best Demo Award. He also presented his tool at this year's Black Hat USA, a famous international hacker conference. Because of this success and the high level of interest from the academic and business worlds, Cappers, his brother Dennis and TU/e PhD student Josh Mengerink founded the start-up AnalyzeData to market Eventpad.
Bram Cappers will receive his PhD on Tuesday 4 December at 16.00 for his thesis ‘Interactive Visualization of Event Logs for Cybersecurity’. He conducted his research under the supervision of prof.dr.ir. Jack van Wijk and prof. dr. Sandro Etalle. TNO, SecurityMatters and Synerscope were also involved as partners.